Let’s talk about the use of attack logs in Defense Base Act claims.
These incredibly helpful logs, which many contracting companies maintain in the regular course and scope of business, are directly relevant to the existence of working conditions which could have caused or contributed to a DBA claimant’s injury. Yet, some insurance carriers often try to hide this discoverable information. Some have even claimed that they “have no records of attacks relating to Claimant or Employer’s property” even though they have attack logs (and more) in their possession. That’s a lie.
So, I am going take the mystery out of attack logs. I am going to explain what they are, why they are relevant, what insurance carriers use them for, how the Office of Administrative Law Judges have responded to motions to compel, and how it prejudices a claimant when an insurance carrier hides relevant information. Finally, I will give a brief example of additional employer-created documents evidencing the existence of attacks.
What are “Attack Logs”?
I use the term “attack logs.” Others say “attack lists.” Basically, it is a list of attacks that a military base experienced.
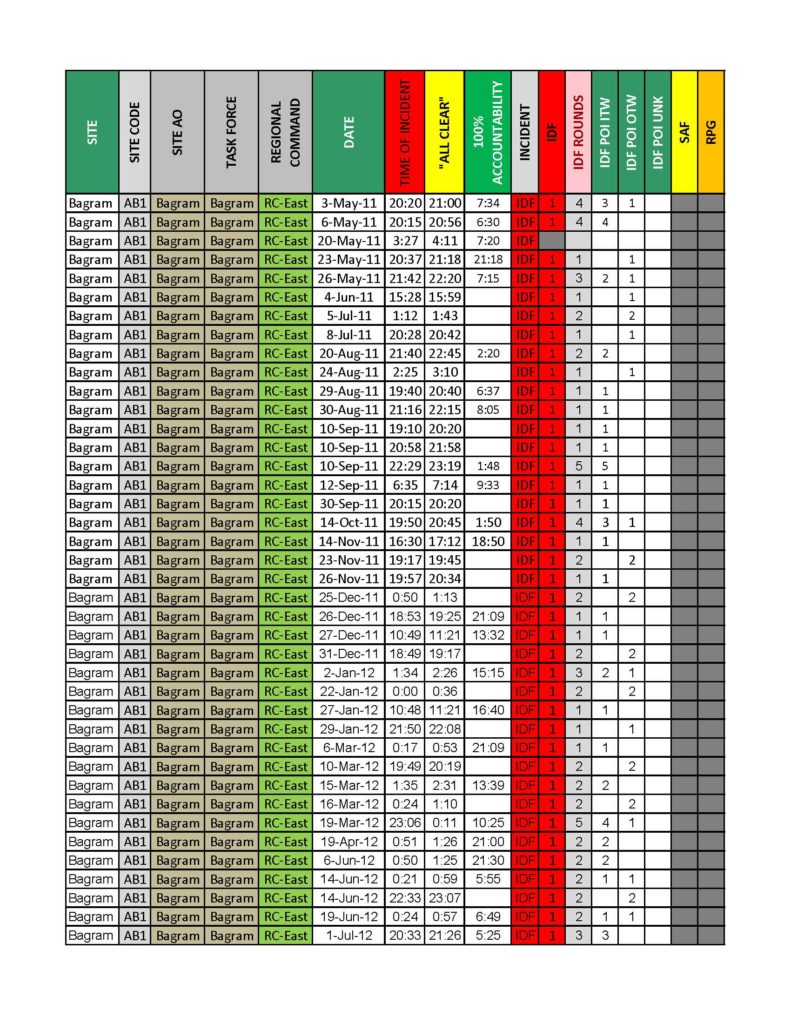
The attack logs can be very specific. For instance, the top photo on this blog post is an attack log from one of the largest LOGCAP defense contractors. The log identifies the location, date, start time, and end time of each attack. The type of attack is identified, too.
This post’s featured photo is only the tip of the iceberg–a jpeg image created from the first page of a lengthy pdf file. But, really, the employer and its insurance carrier should produce the spreadsheets on which attack logs are maintained. Excel spreadsheets provide a description of the event, which is often cut off when insurance carrier attorneys produce a pdf file of the spreadsheet.
Why are Attack Logs Relevant?
In Defense Base Act claims, an injured worker must state a prima facie case. One element of a prima facie case is the existence of working conditions that could have caused the harm. See, e.g., U.S. Indus./Fed. Sheet Metal, Inc. v. Dir., OWCP, 455 U.S. 608, 615 (1982); Ramsay Scarlett & Co. v. Dir., OWCP, 806 F.3d 327, 330 (5th Cir. 2015); Rainey v. Dir., OWCP, 517 F.3d 632, 634 (2d Cir. 2008).
In many psychological injury claims, attack logs prove the existence of working conditions. Plain and simple.
Of course, that is not the only reason that attack logs are relevant. The logs could support the claimant’s credible testimony about injurious events; buttress Criterion A of a PTSD diagnosis or the criteria of other psychological disorders; discredit disingenuous defense doctors who claim that repeated attacks in war zone employment are not traumatic; and more.
Carriers Use Attack Logs, Too:
Insurance carriers know that attack logs prove the existence of injurious working conditions. In fact, they bank on the value of attack logs–but not in the injured worker’s DBA claim. The insurance carriers use attack logs when they request War Hazards Compensation Act reimbursement.
Very generally, injured workers are paid pursuant to the DBA. If the injured worker’s injury was caused by a “war-risk hazard,” then the carrier may apply to the United States government to pay back all of the money paid to the injured worker. Reimbursement is made pursuant to the War Hazards Compensation Act. The carrier is reimbursed for the money it paid to the claimant, as well as the money that it paid for litigation costs and experts. Insurance carriers can literally make a profit on certain DBA/WHCA claims.
Carriers want attack logs from employers to support their application for WHCA reimbursement. Take a look at FECA Bulletin No. 18-03, which defines what a carrier must prove to get reimbursed in psychological injury claims.
If the insurance carrier can prove that the injured worker was present on a base at the time it was attacked, then the United States government will reimburse the insurance carrier for the money it paid in a DBA claim. That’s it. And if the attack log is relevant to the insurance carrier’s WHCA reimbursement claim, which is inextricably intertwined with the injured worker’s DBA claim, then the attack log is relevant for the injured worker, too.
So, carriers gather attack logs to prove that the base was attacked. Then, carriers produce the injured worker’s travel logs to prove that the claimant was present on a particular base at the time that base was attacked.
What is a Travel Log?
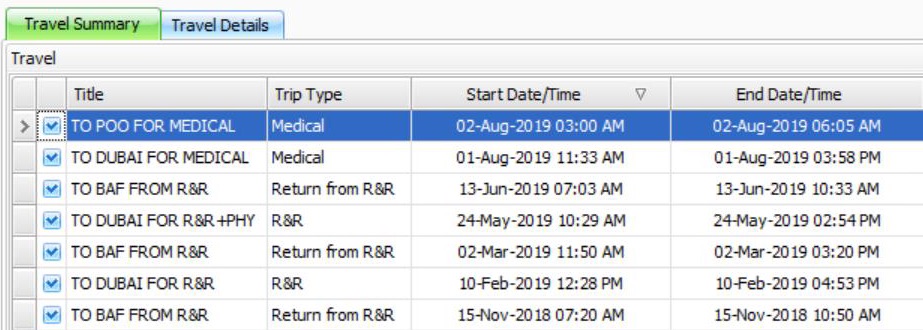
Travel logs are important because they can pinpoint when a claimant was present at a particular location. In the example photograph, there are three locations identified: Bagram Airfield, Dubai, and Point of Origin. Depending on the injury, if the claimant was on a military base when that base came under attack, then he can prove the exposure to working conditions that could have caused a harm. According to FECA Bulletin 18-03, the same is true for a carrier seeking reimbursement.
How Have Judges Addressed Attack Logs?
Some insurance carriers insist on starting discovery disputes about attack logs. Administrative law judges have reasoned that attack logs are discoverable. See 29 C.F.R. 18.51.
Here’s my favorite language from an ALJ, which I often quote in these discovery disputes:
I find the request information is discoverable. Although Claimant is aware of having experienced attacks while stationed, she may not have maintained copies of exact dates and locations of the attacks. The Memorandum of Record produced by the military does not provide dates of the attacks. If this information is Employer’s possession, it is discoverable and relevant. Employer is hereby directed to provide Claimant with a listing of attacks occurring at her job locations during the time she was stationed at each location. Employer may direct Claimant to a produced document in lieu of typing out the response. If the requested information is contained within Claimant’s personnel file, Employer is directed to specifically identify the responsible documents by page number if the documents are paginated or by other means of specific identification.
Quite simply, the information is discoverable. It is disingenuous for an insurance carrier to claim otherwise. The unspoken truth about DBA/WHCA claims is that WHCA reimbursement is the first consideration an insurance carrier makes when it receives notice of a new DBA claim.
For example, when Gallagher Bassett receives a new Defense Base Act claim, it contacts the employer and asks for documents and information. Specifically, Gallagher Bassett starts its claims by asking for:
- Wage statements showing all wages and compensation paid;
- A copy of the job description, including physical limitations;
- The employee’s personnel file, including the employee’s International Assignment Provisions, job application, resume, and offer of employment;
- Any available medical records;
- Any available Employees’ Assistance Program notes–which, as an aside, is very troubling consider the fact that many employees voluntarily seek help under the impression that the information shared is confidential. The employer, the insurance carrier’s adjuster, and the insurance carrier’s attorneys all see EAP notes before the claimant or the claimant’s attorney;
- The employee’s pre-employment medical questionnaire and all deployment-related medical records;
- The employee’s travels logs; and
- Base attack logs identifying specific war-risk hazard incidents that occurred on the employee’s base.
Despite all of this information changing hands between the employer and the insurance carrier’s third party administrator at the start of a claim, most of this information is not provided to the DBA claimant or the claimant’s attorney while the case is pending at the Office of Workers’ Compensation Programs. Why not? It’s discoverable. The claimant is certainly allowed to review that information. Perhaps every employer and the OWCP need to audit how certain insurance carriers and third party administrators handle claims on the employer’s behalf.
It Prejudices Claimants When Carriers Hide Evidence:
I’ve seen some insurance carriers argue that they are prejudiced if they do not get to depose a claimant before producing attack logs. No, really. They argue that they are entitled to hide relevant information–you know, information that the claimant wants to address at his deposition–in some weird attempt to play “Gotcha!” at the deposition.
Near as I can tell, the argument goes something like this: if claimant cannot state the exact date that he experienced rocket and mortar fire, then that rocket and mortar fire must not have happened. That’s silly. The rules of evidence are more relaxed in administrative law proceedings, but that doesn’t mean that a claimant cannot reference writings to refresh his recollection, authenticate attack photos, or reference newspapers and government-funded attack databases like the Global Terrorism Database. The claimant has already stated that he was exposed to many injurious attacks–attacks that the claimant lived through. The claimant would like to talk about those attacks–all of those attacks–at his deposition. The claimant is allowed to reference attack logs while doing so, and he is prejudiced when insurance carrier’s hide that information. To go back to my favorite ALJ language regarding attack logs: “Although Claimant is aware of having experienced attacks while stationed, she may not have maintained copies of exact dates and locations of the attacks. If this information is Employer’s possession, it is discoverable and relevant.” An argument that this evidence is somehow “potential impeachment evidence” falls flat.
Another argument that I’ve heard lately is that the insurance carrier will not provide attack logs until the injured worker and the injured worker’s attorney consents to an employer-drafted confidentiality agreement. Quite simply, there is no basis for such an agreement, which infringes upon protected rights. Just consider the following:
- The insurance carrier has likely already disclosed most of the attack logs to the United States government when the insurance carrier applied for War Hazards Compensation Act reimbursement. the carrier cannot claim in a later case that the same attack log enjoys a qualified privilege that allows government disclosure but not disclosure to an adverse party. Cf. In re Columbia/HCA Healthcare Corp. Billing Practices Litigation, 293 F.3d 289, 302-04 (6th Cir. 2002).
- There is a presumptive right, in part protected by the First Amendment, to share what is learned in discovery. Litigants can share the information with anyone, including the media. This right exists not just for the litigants but, in disputed claims, for the public as well. Caterwauling for a “confidentiality agreement” doesn’t mean that a litigant is required to give up their rights–especially when the carrier intends to break the confidentiality agreement as soon as the DBA claim resolves and it can request WHCA reimbursement.
- There is no good cause for confidentiality or a protective order. Again, we are talking about a relevant list of events–foreseeable events according to employment contracts–that the claimant experienced firsthand. There is no way for the carrier to show annoyance, embarrassment, oppression, or undue burden. Providing attack logs is as simple as cutting and pasting a master Excel spreadsheet into a claimant-specific Excel spreadsheet.
- Efficient discovery in other cases is a sufficient justification for modifying protective orders. As such, it is most definitely sufficient justification for denying a baseless motion for a protective order in the first instance.
- Every mental health claim that proceeds to formal hearing will include attack logs–including those claims where carriers dishonestly allege that no such evidence exists. If that claim climbs its way up to the Benefits Review Board and then to district or appellate courts, then attack logs will definitely make their way to PACER.
Finally, some carriers take the self-serving position that the attack logs are sensitive and could potentially impact national security. Yet, those same carriers voluntarily disclose the exact same information to get their WHCA reimbursement. These carriers will (1) negotiate a DBA settlement with a claimant, (2) send the claimant a “War Hazards Affidavit” and attack logs to confirm exposure to the events listed on the logs, and (3) submit the War Hazard Affidavit and attack logs to the Division of Federal Employees’, Longshore and Harbor Workers’ Compensation as evidence to support the carrier’s application for WHCA reimbursement. Carriers use this same procedure in case after case, again and again–meaning that it has already disclosed the same attack logs to many, many people. So, am I to take it that an insurance carrier’s alleged fidelity to “national security” is steadfast only until the carrier can recover a large chunk of money? Because that’s what it sounds like.
And, of course, none of the carriers’ arguments are ever accompanied by a privilege log.
…And It’s Not Just Attack Logs:
While this post is limited to attack logs, there is a host of other evidence that also proves the existence of attacks, which directly relates to the working conditions aspect of many claimants’ prima facie claims.
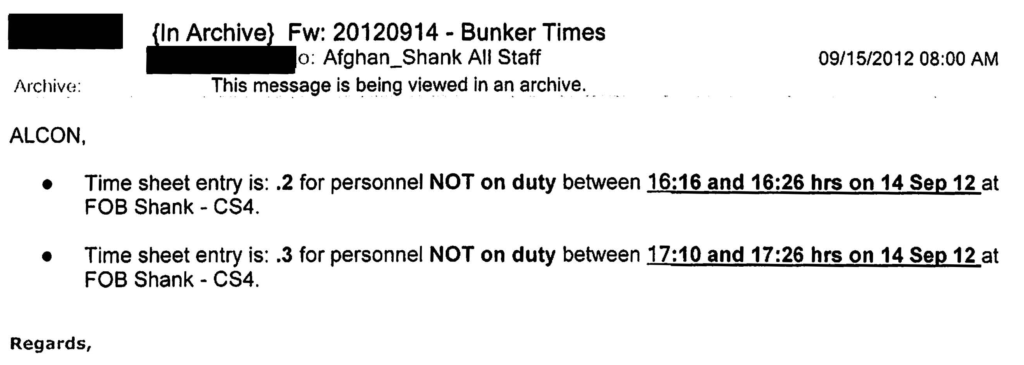
For example, there are Bunker Time e-mails…
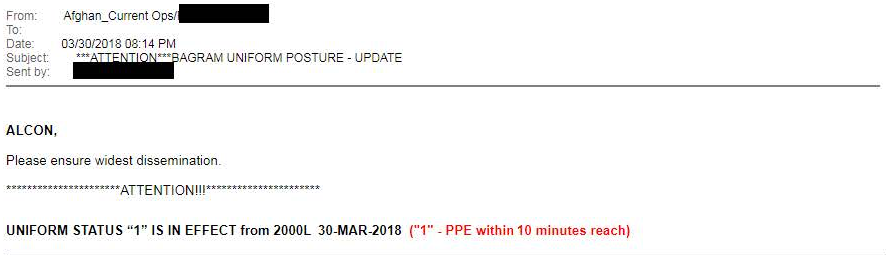
There are Uniform Posture Upgrade e-mails…
There are SPOT Reports…
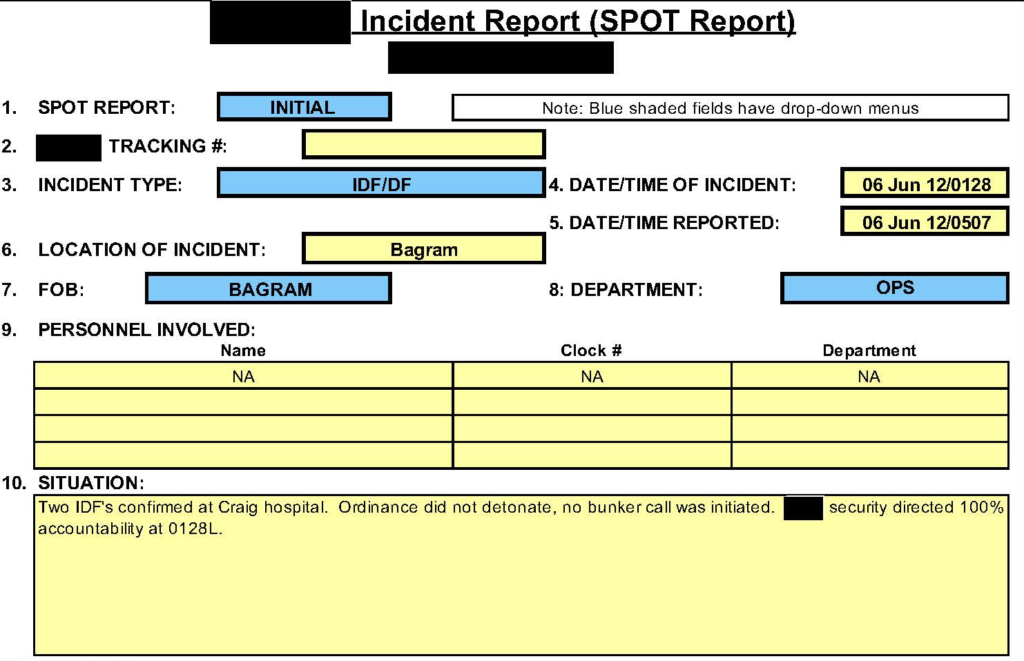 Really, the list goes on and on. All of the documents are relevant. All the documents are prepared in the regular course and scope of business. And all of the documents will be used eventually by the insurance carrier to request reimbursement under the War Hazards Compensation Act–which is the carrier’s plan from Day One.
Really, the list goes on and on. All of the documents are relevant. All the documents are prepared in the regular course and scope of business. And all of the documents will be used eventually by the insurance carrier to request reimbursement under the War Hazards Compensation Act–which is the carrier’s plan from Day One.
Conclusion:
It’s the hypocrisy that irks me. Insurance carriers hide a wealth of information that actually confirms the existence of injurious working conditions. They complain about prejudice for producing documents confirming the very allegations made by the injured worker. And why? So they can play “Gotcha!”? So they can curb efficient discovery amongst people who experienced firsthand the same attacks? Quite simply, workers don’t walk around Bagram Airfield or Al Asad Airbase with a diary, recording the date and time of every rocket, mortar, and missile attacks. And they don’t have to. The evidence exists and it is readily discoverable. Kudos to the carriers and attorneys who readily provide this discoverable information, thus saving tens of thousands of dollars and many, many litigation hours.
